Research Projects
- Advancing Dietary Recall among Older Adults Using Conversational Artificial Intelligence (2021-Now)
- Geriatric Functional Assessment System Using Passive Wearable Sensing and Deep Learning (2023-Now)
- NIH/NIA R01: SCH: INT: Collaborative Research: Exploiting Voice Assistant Systems for Early Detection of Cognitive Decline (2019-2025)
- NSF/NeTS: Towards Privacy-Preserving Autonomous Vehicle Sharing Services (2016-2020)
- Enhancing Security, Privacy and Characteristic Inference of Voice Assistant Systems (2018-now)
- Wireless Signals and Channel State Information for Physical Sensing (2016-now)
- Google Internet of Things Research Award(2016-2017)
- Secure Wearable Applications (2014-2017)
- Security, Privacy, and Trustworthiness in Healthcare (2010-now)
- Security and Privacy in Mobile Social Networks (2010-2013)
- Secure Smartphone-based Namecard Exchange (2013)
Advancing Dietary Recall among Older Adults Using Conversational Artificial Intelligence (2021-Now)
Use of dietary assessments in efficacy-based interventions can lead to improved morbidity, prevention of cancer, and reduction of the risk of death. However, standard 24-hour recalls, such as the NCI's Automated Self-Administered 24-hour (ASA-24) assessment, are complex, lengthy, and lead to challenges in collecting reliable and consistent intake data, particularly in real-world settings. Implementation of such tools is even more complicated in older adults with declining declarative memory, lower technology literacy, and accessibility issues. This population relies on specific dietary strategies to assess and monitor their chronic diseases. Recalls also assist practitioners in uncovering early signs of malnutrition or acute illness. We aim to optimize and validate a novel FOod REcall Artificial Intelligence-based SpEEch (FORESEE) system that assesses an individual's food intake. The FORESEE system will be implemented on voice assistants (e.g., Google Home, Amazon Alexa) and will be adapted to address gaps in dietary assessments by integrating diet-specific conversational artificial intelligence that informs dietary questioning, recognizes responses to questions, and enables clarifying strategies. Our outcomes will ensure FORESEE has comparable system accuracy, shorter session length, higher system usability (based on the System Usability Scale), >=85% validity for assessing food items, and a low root-mean-square error score for assessing food quantity using the ASA-24 as a baseline. Our pilot data has shown promising feasibility and acceptance criteria of our voice-based food recall prototype, users' experiences and preferences of clarifying strategies that address conversation failure, input from end-user interviews (older adults, registered dietitian nutritionists), and enhanced accuracy of speech and language methods that can be used herein. A functioning system will allow future integration with ASA-24 data modules and pathways to derive profiles at the nutrient level. This will permit FORESEE to learn, gather, and recognize multiple, longitudinal dietary recalls and patterns via personalized artificial intelligence to improve the management of this high-risk group.
Geriatric Functional Assessment System Using Passive Wearable Sensing and Deep Learning (2023-2025)
Physical function declines with age, making it increasingly difficult for older adults to live independently. Primary care providers are well-positioned to screen for early signs of functional decline. A Geriatric Functional Assessment (GFA) system consisting of a badge-like wearable worn during visits will be designed to collect visual and motion data unobtrusively. After building the prototype, we will conduct a usability study on 21 older adults. We will use deep neural networks to analyze this data and infer physical function. This system will assess physical function allowing clinicians to implement interventions to promote and maintain healthy aging.
NIH/NIA R01: SCH: INT: Collaborative Research: Exploiting Voice Assistant Systems for Early Detection of Cognitive Decline (2019-2023)
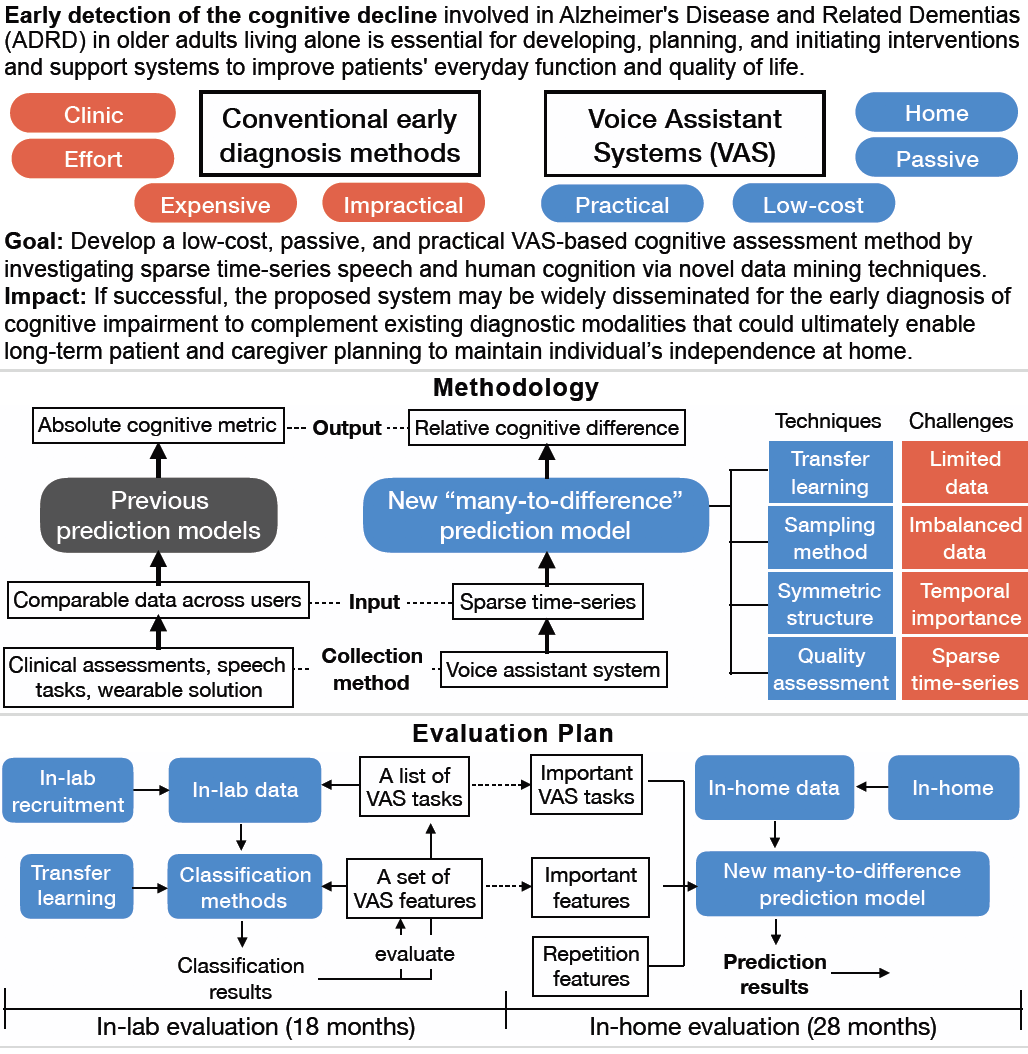
Early detection of the cognitive decline involved in Alzheimer's Disease and Related Dementias (ADRD) in older adults living alone is essential for developing, planning, and initiating interventions and support systems to improve patients' everyday function and quality of life. Conventional, clinic-based methods for early diagnosis are expensive, time-consuming, and impractical for large-scale screening. This project aims to develop a low-cost, passive, and practical home-based assessment method using Voice Assistant Systems (VAS) for early detection of cognitive decline, including a set of novel data mining techniques for sparse time-series speech. If successful, the proposed system may be widely disseminated for the early diagnosis of cognitive impairment to complement existing diagnostic modalities that could ultimately enable long-term patient and caregiver planning to maintain individual's independence at home.
NSF/NeTS: Towards Privacy-Preserving Autonomous Vehicle Sharing Services (2016-2020)
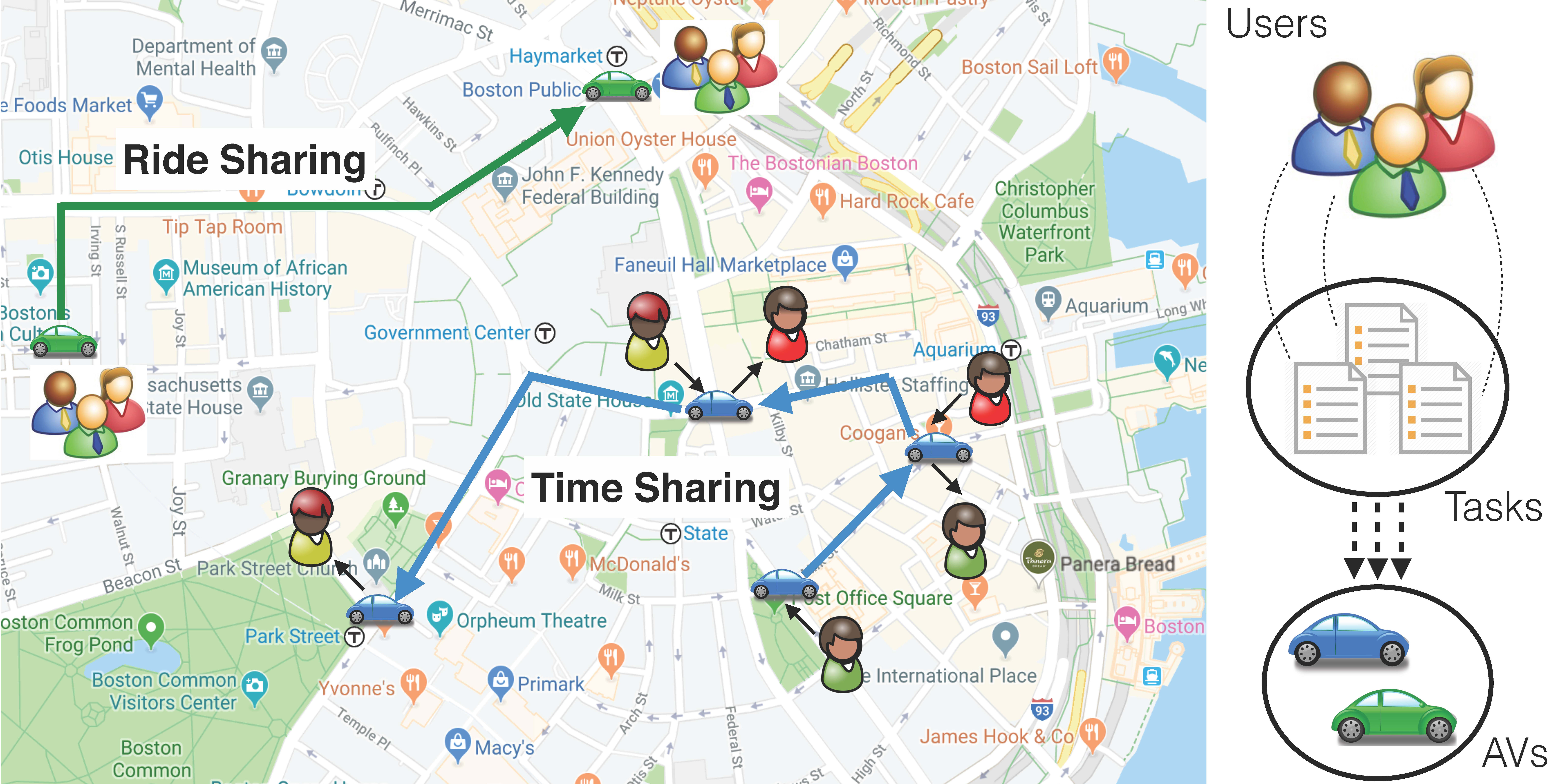
Over the past several years, the automobile and technology industries have made significant leaps in bringing computerization and automation
to car driving. Autonomous Vehicles (AVs) have the potential to fundamentally improve transportation systems by dramatically reducing crashes,
assisting traffic flows, reducing travel time and energy consumption, providing critical mobility to the elderly and disabled, and making vehicle
sharing convenient, popular, and necessary. This project studies the architecture and privacy issues related to autonomous vehicle sharing (AVS) that
can revolutionize our transportation experience by providing novel time-sharing and ride-sharing services. The time-sharing services allow AVs to be
shared by different users at non-overlapping time periods, while the ride-sharing services allow AVs to be shared by users taking similar trips during
the same time period. With autonomous driving techniques, the quality of both services can be significantly enhanced to benefit commuters. However,
the time- and ride- sharing systems need to communicate with users to organize shared vehicles, which is not risk free. Massive information on users'
activities can be exposed in case of privacy breach. Existing privacy-preserving techniques cannot be applied effectively and efficiently in AVS due
to problems and requirements unique to AVS, e.g., location- and time- sensitive trips and multi-user coordination. This project addresses the unique
privacy problems raised by AVS and proposes effective and efficient privacy-preserving techniques, which can promote AVS among users. The research in
this project will have major technological impacts on privacy-preserving AV sharing services. The project will study the privacy-preserving task
matching problem for the time-sharing service and the privacy-preserving trip searching problem for the ride-sharing service, while computation and
communication overhead, trip delays due to unexpected conditions, costs of transitional trips, users' social preferences, and different privacy
protection levels will be considered.
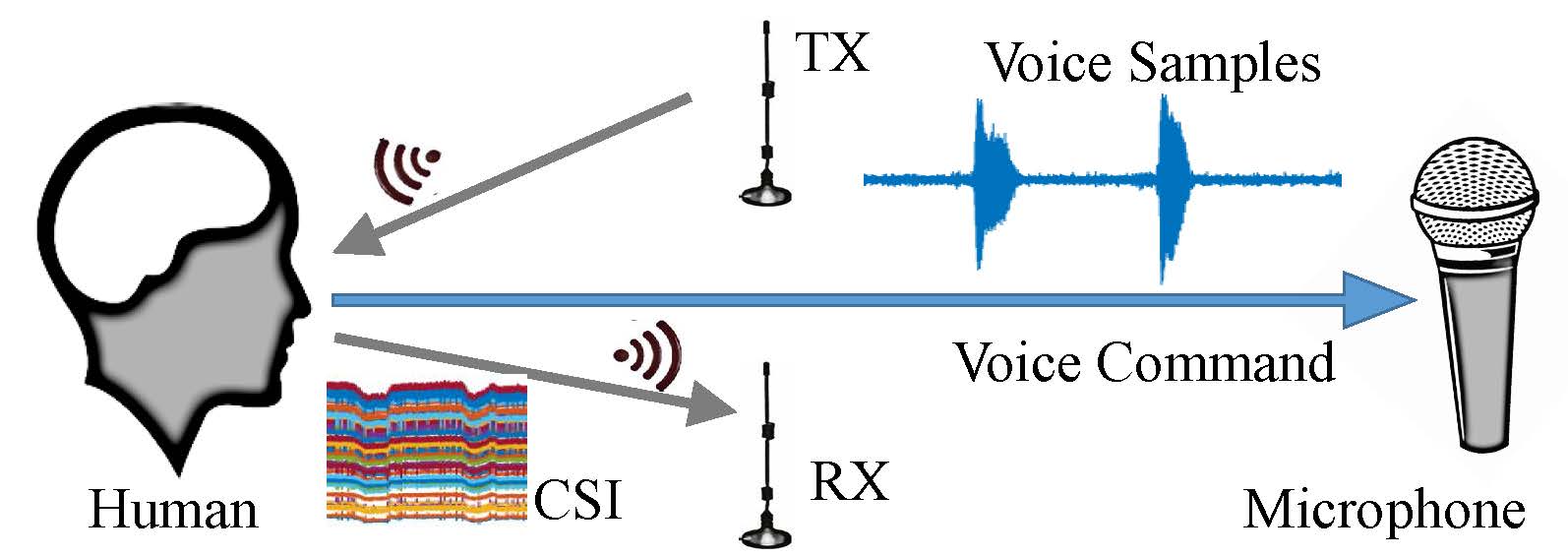
Enhancing Security, Privacy and Characteristic Inference of Voice Assistant Systems (2018-now)
 />
/>
/>
/>
Wireless Signals and Channel State Information for Physical Sensing (2016-now)
[PDF at ACM][Youtube Video]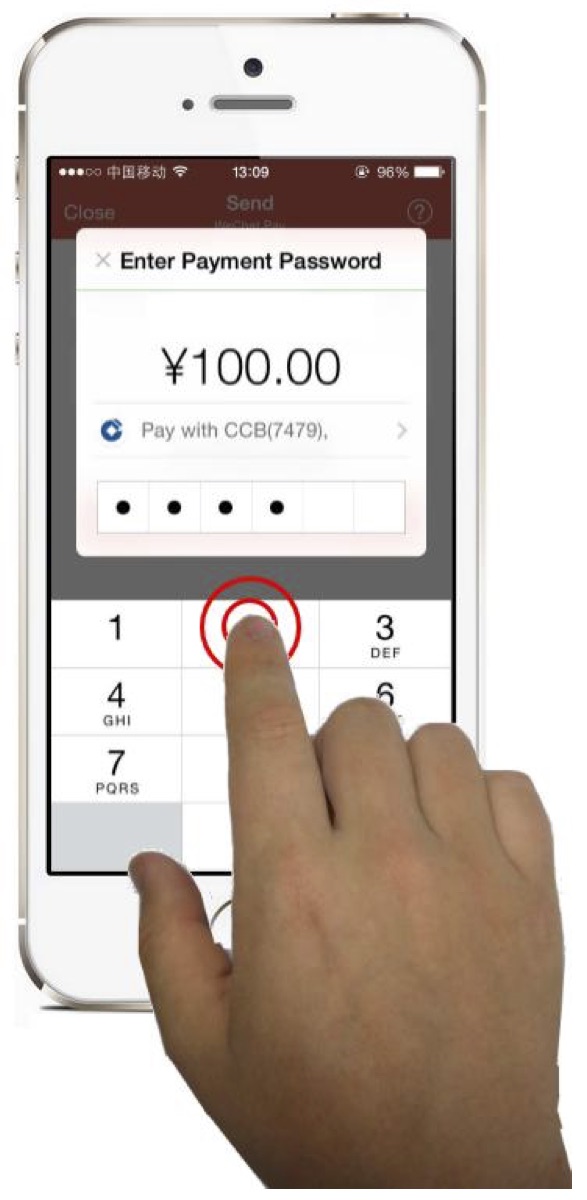
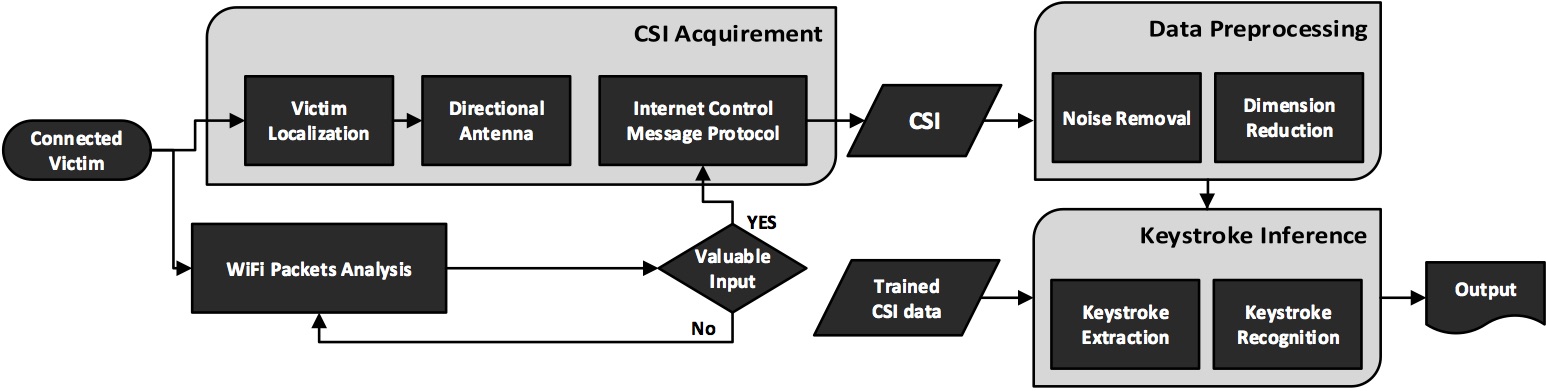
We present WindTalker, a novel and practical keystroke inference framework that allows an attacker to infer the sensitive keystrokes on a mobile device through WiFi-based side-channel information. WindTalker is motivated from the observation that keystrokes on mobile devices will lead to different hand coverage and the finger motions, which will introduce a unique interference to the multi-path signals and can be reflected by the channel state information (CSI). The adversary can exploit the strong correlation between the CSI fluctuation and the keystrokes to infer the user's number input. WindTalker presents a novel approach to collect the target's CSI data by deploying a public WiFi hotspot. Compared with the previous keystroke inference approach, WindTalker neither deploys external devices close to the target device nor compromises the target device. Instead, it utilizes the public WiFi to collect user's CSI data, which is easy-to-deploy and difficult-to-detect. In addition, it jointly analyzes the traffic and the CSI to launch the keystroke inference only for the sensitive period where password entering occurs. WindTalker can be launched without the requirement of visually seeing the smart phone user's input process, backside motion, or installing any malware on the tablet. We implemented Windtalker on several mobile phones and performed a detailed case study to evaluate the practicality of the password inference towards Alipay, the largest mobile payment platform in the world. The evaluation results show that the attacker can recover the key with a high successful rate.
Internet of Things (2016-now)
A project supported by Google.
Fitness tracking has been implemented over smartphones and wearables. While smartphones are often used as activity planner and reminder, wearables act more passively to monitor users' actions, heart rate, brain activity, muscle motion and other critical data that can be affected by the physical activities. However, the smartphones and wearables merely focus on the interaction with users. The lack of awareness of the users' ambient environment leads to inevitable errors in gym activity tracking. For example, with the wearables, it is impossible to tell which weights a user lifts unless a wearable is on the right muscle and keeps monitoring the muscle strength; it is also difficult to tell if a user is running on a treadmill or on the ground, which have a significantly difference in terms of activity intensity. We plan to propose a novel gym activity tracking system using both wearable and IoT technologies to achieve two objectives: Accuracy: the system passively collects the data from the deployed IoT devices in the gym and wearables on the user, and can accurately recognize the gym activities. Usefulness: the system generates user-friendly gym reports as a feedback to users in real-time. The usefulness will be evaluated by an in-gym deployment and a two-week user study.
Secure Wearable Applications (2014-now)
A project started at Dartmouth College.

Wearables are small and have limited user interfaces, so they often wirelessly interface with a personal smartphone/computer to relay information from the wearable for display or other interactions. In this paper, we envision a new method, LightTouch, by which a wearable can establish a secure connection to an ambient display, such as a television or a computer monitor, while ensuring the user's intention to connect to the display. LightTouch uses standard RF methods (like Bluetooth) for communicating the data to display, securely bootstrapped via the visible-light communication (the brightness channel) from the display to the low-cost, low-power, ambient light sensor of a wearable. A screen `touch' gesture is adopted by users to ensure that the modulation of screen brightness can be securely captured by the ambient light sensor with minimized noise. Wireless coordination with the processor driving the display establishes a shared secret based on the brightness channel information. We further propose novel on-screen localization and correlation algorithms to improve security and reliability. Through experiments and a preliminary user study we demonstrate that LightTouch is compatible with current display and wearable designs, is easy to use (about 6 seconds to connect), is reliable (up to 98\% success connection ratio),
and secure against attacks.
Security, Privacy, and Trustworthiness in Healthcare (2010-now)
A project started at the BBCR group of the University of Waterloo.
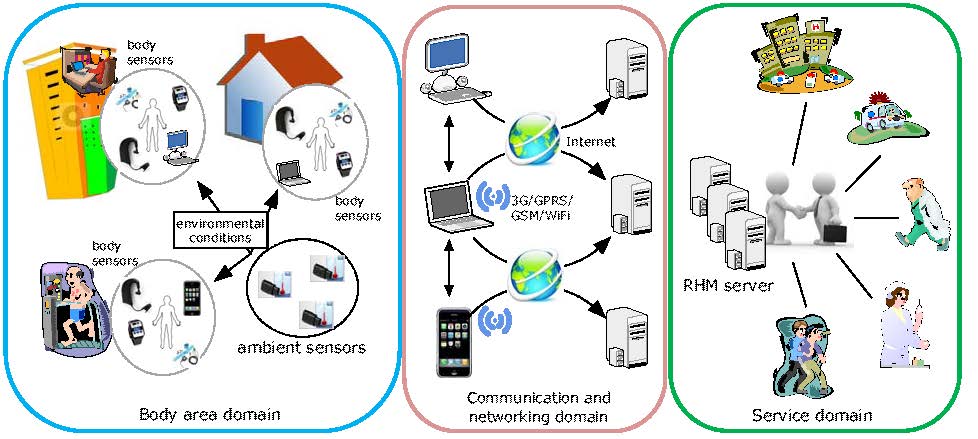
Recent advances in computing technologies including body sensors and wireless communications have revealed the possibility of providing remote health monitoring (RHM) to patients at high risk of falls and with chronic diseases. The body sensors deployed in, on, or around the human body are able to measure the fundamental health parameters in a situation where large-sized and standard medical examination equipments are not available; the pervasive use of mobile phones and the ubiquity of WiFi connection enable medical informatics to overcome the time and location barriers. RHM systems offer long-term real-time individualized medical measures and continuous health data collection. They provide a unique opportunity to shift healthcare tasks from a traditional clinical environment to a pervasive user-centered setting. They allow users to reduce healthcare expenses through more efficient use of clinical resources and earlier detection of medical conditions, which in turn drastically trims the government health budget. By fully utilizing advanced biomedical sensing technologies and wireless communications, RHM systems indeed hold the promise to provide an effective solution to the rising healthcare crisis. In this project, we study many security and privacy problems from health perspective, e.g., patient self-control access policy, symptom-based secret handshake, routing problems of wireless body area networks, and secure and trustworthy health information exchange with the assistance of cloud services, vehicular communication, and social networks.
Security and Privacy in Mobile Social Networks (2010-2013)
A project started at the BBCR group of the University of Waterloo.
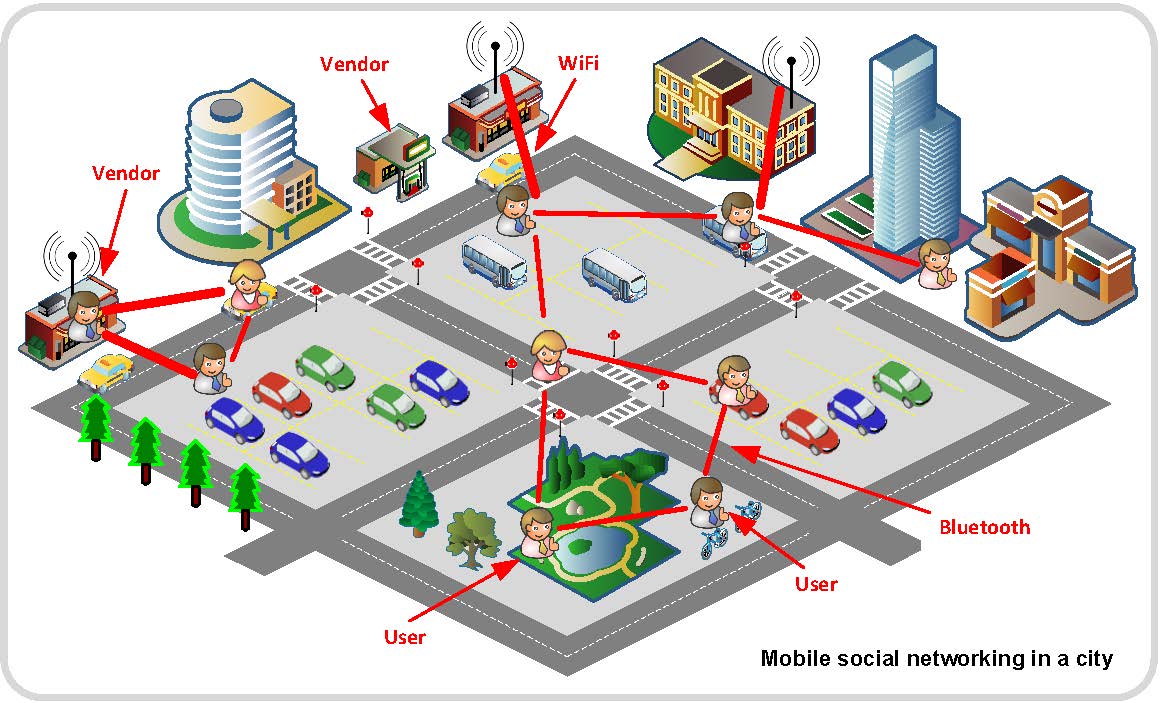
This project focuses on three emerging research topics in mobile social networks (MSNs): privacy-preserving profile matching (PPM) protocols, privacy-preserving cooperative data forwarding (PDF) protocols, and trustworthy service evaluation (TSE) systems. The PPM helps two users compare their personal profiles without disclosing the profiles. The PDF helps users forward data to their friends via multiple cooperative relay peers while preserving their identity and location privacy. The TSE enables users to locally share service reviews on the vendors such that users receive more valuable information about the services not only from vendors but also from their trusted social friends. We addressed both theoretic and practical aspects of these topics by introducing the system model, reviewing the related works, and presenting the solutions. We further provided the security analysis and the performance evaluation based on real-trace simulations.
Secure Smartphone-based Namecard Exchange (2013)
A project started at the BBCR group of the University of Waterloo.
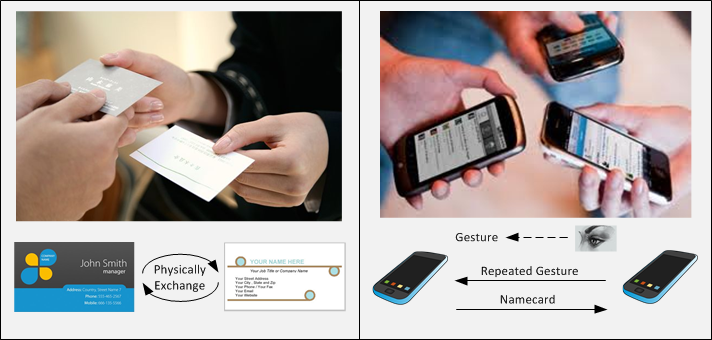
This project aims to study an interesting smartphone application, called secure NAMECARD exchange, where two users are able to exchange name cards in public places, such as conference sites and restaurants. Namecard exchange is a very common social activity. With smartphones, users could easily build their profiles as electronic name cards (e-cards) and fairly exchange with others. The e-card is easy-to-use and cost-saving. Gesture-based Electronic naMecard (GEM) is an advanced smartphone application that helps users exchange e-cards in a casual situation. GEM applies Gesture Recognition and Jave Pairing Based Cryptography (JPBC) to secure the exchange of e-card from eavesdropping and modification attacks.