| |
| |
NeTS: Small: Collaborative Research: Towards Privacy-Preserving Autonomous Vehicle Sharing Services
Sponsored by the U.S. National Science Foundation (Awards # CNS-1618893 and CNS-1618549)
Duration: 09/01/2016-8/31/2020
 
|

|
Welcome to the website of our research project: "NeTS: Small: Collaborative Research: Towards Privacy-Preserving Autonomous Vehicle Sharing Services" by the University of Massachusetts Boston and Tennessee Technological University.
Synopsis
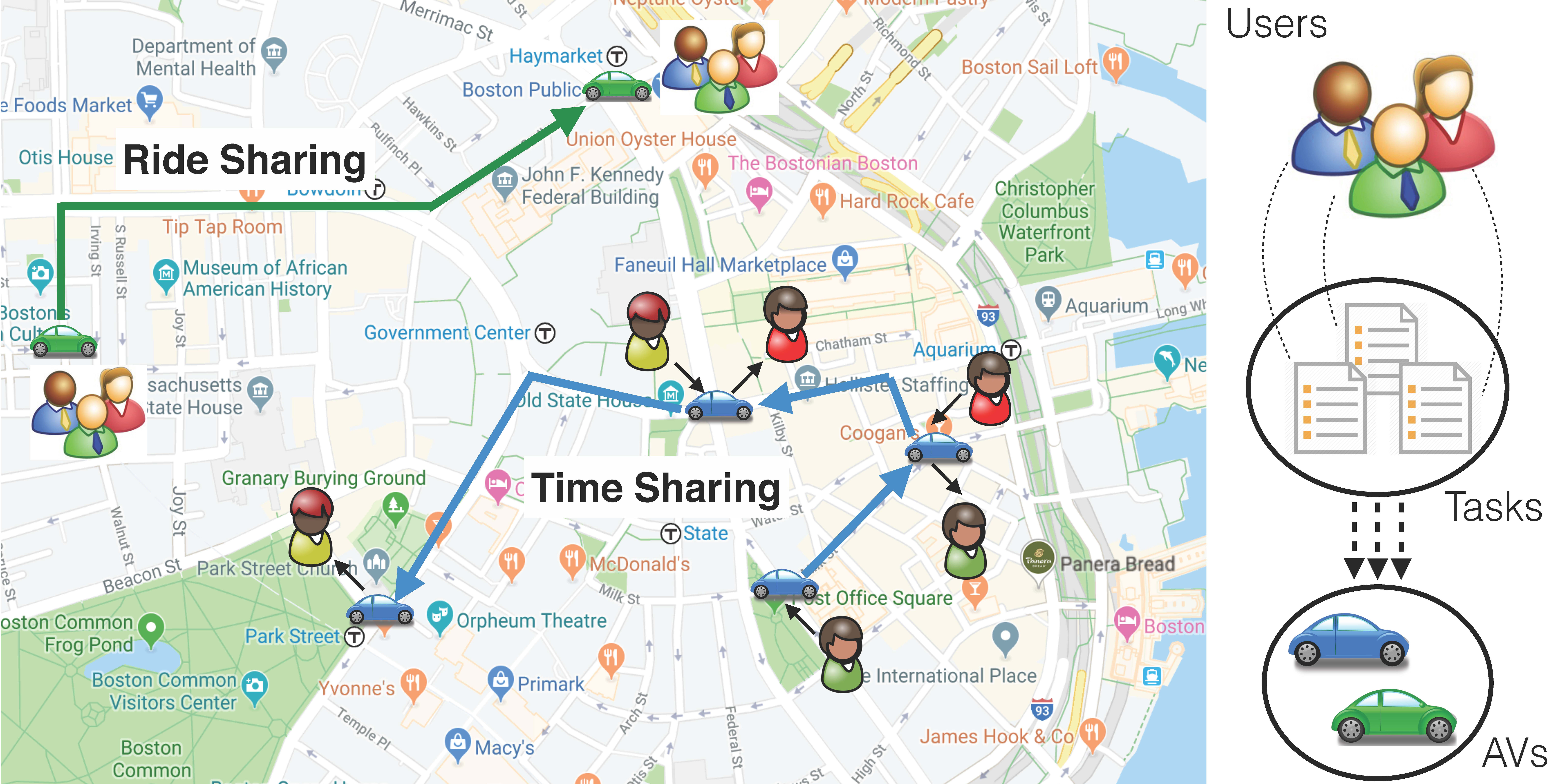
Over the past several years, the automobile and technology industries have made significant leaps in bringing computerization and automation to car driving. Autonomous Vehicles (AVs) have the potential to fundamentally improve transportation systems by dramatically reducing crashes, assisting traffic flows, reducing travel time and energy consumption, providing critical mobility to the elderly and disabled, and making vehicle sharing convenient, popular, and necessary. This project studies the architecture and privacy issues related to autonomous vehicle sharing (AVS) that can revolutionize our transportation experience by providing novel time-sharing and ride-sharing services. The time-sharing services allow AVs to be shared by different users at non-overlapping time periods, while the ride-sharing services allow AVs to be shared by users taking similar trips during the same time period. With autonomous driving techniques, the quality of both services can be significantly enhanced to benefit commuters. However, the time- and ride- sharing systems need to communicate with users to organize shared vehicles, which is not risk free. Massive information on users' activities can be exposed in case of privacy breach. Existing privacy-preserving techniques cannot be applied effectively and efficiently in AVS due to problems and requirements unique to AVS, e.g., location- and time- sensitive trips and multi-user coordination. This project addresses the unique privacy problems raised by AVS and proposes effective and efficient privacy-preserving techniques, which can promote AVS among users. The research in this project will have major technological impacts on privacy-preserving AV sharing services. The project will study the privacy-preserving task matching problem for the time-sharing service and the privacy-preserving trip searching problem for the ride-sharing service, while computation and communication overhead, trip delays due to unexpected conditions, costs of transitional trips, users' social preferences, and different privacy protection levels will be considered.
Personnel
Principal Investigators
Formal Graduate Students
 |
Mohammad Hadian (UMass Boston Ph.D. Fall 2016 - Spring 2019)
Assistant Professor
Department of Computer Science
Clark University
Email: mhadian@clarku.edu
Homepage: https://mathcs.clarku.edu/~mhadian/ |
 |
Thamer Altuwaiyan (UMass Boston Ph.D. Fall 2015 - Spring 2019)
Assistant Professor
Department of Computer Science
Shaqra University
Email: thamerfa@cs.umb.edu
Homepage: https://www.cs.umb.edu/~thamerfa/ |
 |
Ahmed Sherif (TTU Ph.D. Sept. 2015 - July 2017)
Assistant Professor
Department of Computer Engineering
University of Southern Mississippi
Email:
Homepage: https://www.usm.edu/computing/faculty/dr-ahmed-sherif |
Current Graduate Students
 |
Bang Tran (Jan. 2019 - )
Ph.D. student
Department of Computer Science
University of Massachusetts Boston
Email: Bang.Tran001@umb.edu
Homepage: https://www.cs.umb.edu/~bangtqh/ |
 |
Mohamed Baza (May 2018 - )
Ph.D. student
Department of Electrical and Engineering
Tennessee Technological University
Email:
Homepage: |
 |
Mahmoud Nabil (Jan. 2017 - )
Ph.D. student
Department of Electrical and Engineering
Tennessee Technological University
Email:
Homepage: |
 |
Chenjun Li (June 2019 - )
Master student
Department of Computer Science
University of Massachusetts Boston
Email: Chenjun.Li001@umb.edu
Homepage: |
Publications
- (New Journal Paper)Exploiting Peer-to-peer Communications for Query Privacy Preservation in Voice Assistant Systems,
Bang Tran and Xiaohui Liang,
Peer-to-Peer Networking and Applications, Springer, 2020.
Summary: Voice assistant system (VAS) is a popular technology for users to interact with the Internet and the Internet-of-Things devices. In the VAS, voice queries are linked to users’ accounts, resulting in long-term and continuous profiling at the service provider. In this paper, we propose a VAS anonymizer aiming to mix the queries of the VAS users to increase the source anonymity. The VAS anonymizer is equipped with a pattern-matching scheme, which allows VAS devices to find effective peer relays without disclosing their query patterns. Furthermore, the VAS anonymizer is equipped with anonymity evaluation modules for evaluating real-time single query, thus reducing the risk of pattern violation at the relays. Both the requester and the relay will evaluate the real-time query based on the resulting anonymity. Only if the anonymity evaluations at both requester and relay are positive, the query will be sent to the service provider via the relay. The VAS anonymizers at VAS devices coordinate the query uploading such that the sources of the queries are anonymized, and the service provider is unable to link the voice queries to individual users. In the experiments using our customized VAS devices and the Amazon Cloud servers, the computation and communication overhead of the matching scheme is shown to be efficient, and the anonymity evaluation modules are shown to be effective in protecting the privacy of the requesters and the relays.
- (New Conference Paper)Exploiting Privacy-preserving Voice Query in Healthcare-based Voice Assistant System,
Thamer Altuwaiyan, Mohammad Hadian, Samuel Rubel, and Xiaohui Liang,
IEEE International Conference on Communications (ICC, 2020.
Summary: Voice Assistant Systems (VAS) such as Amazon Echo and Google Home are becoming a popular technology for medical health systems among patients and caregivers. The VAS devices allow patients and caregivers to interact with them via voice commands. In most cases, the users' private voice data is fully disclosed to the VAS server, which may raise severe privacy concerns, especially in case of medical information which are clearly sensitive. In this paper, we propose a privacy-preserving voice query scheme in the healthcare-based voice assistant system, which enables the users to use voice commands for uploading medical data and later retrieving them. The VAS server in this case has no access to the original voice command or the data stored but it can accurately respond to user's query. Our scheme consists of two voice matching techniques with weak and strong privacy levels, where the former discloses only the voice feature, and not the original voice to the server. The latter further uses an obfuscation function to hide the voice features, thus the data is fully protected. We evaluate the performance of our proposed scheme by conducting experiments on self-generated voice data set, from three different languages, English, Chinese, and Arabic. We prove that our proposed scheme can achieve the privacy preservation of the voice data, and up to 98% accuracy in responding to voice queries.
- (New Conference Paper) Exploiting Physical Presence Sensing to Secure Voice Assistant Systems,
Bang Tran, Shenhui Pan, Xiaohui Liang, and Honggang Zhang,
IEEE International Conference on Communications (ICC), 2021.
Summary: Voice Assistant System (VAS) provides a convenient way for users to interact with smart-home devices via a voice interface. However, it raises unique security issues, including voice replay and injection attacks, where attackers remotely and maliciously control the smart-home devices via a voice interface. In this paper, we consider a typical smart-home scenario in which a VAS device and a compromised speaker device are placed in close physical proximity. The attacker can remotely play malicious voice commands through the speaker device to manipulate the VAS device for malicious purposes. We propose a defense system on the VAS device to secure the VAS device against both voice replay and injection attacks, without any additional devices and without any extra user effort. Specifically, our system aims to collect voice data and wireless data continuously from the VAS device. Our system then extracts the Mel-Cepstral Frequency Coefficients (MFCC) features from voice and wireless data. We consider that both voice and wireless data are affected by the same present users' physical activities, and the correlation can be used to detect the attacks. Finally, our system applies a deep learning model that learns from previous time-series data and analyze real-time data to infer whether the real-time voice command is generated from a user or a speaker device. We have tested our system in certain real-world smart-home scenarios. Our experiments showed that the proposed system has a probability between 76.4% to 89.1% to successfully detect the voice replay and injection attacks in the considered scenarios.
- Privacy-preserving Task Scheduling for Time-sharing Services of Autonomous Vehicles,
Mohammad Hadian, Thamer Altuwaiyan, Xiaohui Liang, and Haojin Zhu,
IEEE Transactions on Vehicular Technology, Vol. 68, No. 6, June 2019.
Summary: Sharing of autonomous vehicles between multiple users can potentially be the ultimate solution for increasing the efficiency of the transportation system. In a time-sharing scenario, autonomous vehicles (AV) owners share their vehicles to others at their unwanted times without incurring any human efforts. However, such sharing service requires the disclosure of users' locations and route information, raising severe privacy concerns and issues. In this paper, we propose a privacy-preserving task scheduling scheme for time-sharing services of autonomous vehicles. First, we design a matching scheme that finds the feasible requesters for each available AV. Then, we propose a scheduling scheme using different approaches for assigning requesters to the AVs based on different system parameters. Both schemes work efficiently without requiring users to share their exact locations and route details while maximizing the AV owner profit and minimizing the requester cost. Specifically, our schemes enable an untrusted matching server to match owners and requesters using a set of intermediate destination (ID) locations in the travel paths. Only if the service can be given to the requester efficiently, the owner and the requester share the details of the routes. All the calculations for verification of the feasibility of the service are done on the untrusted server. We show the accuracy of our proposed scheme through extensive simulations on real data. The results confirm that our traffic-based ID selection scheme, with consideration of the traffic information and patterns in the area, outperforms the baseline scheme where the IDs are chosen randomly. Furthermore, the effectiveness of different scheduling schemes including greedy-based and first come first served are evaluated.
- Enhancing User-Oriented Security and Privacy in Emerging Data Sharing and Sensing Services,
Mohammad Hadian,
UMB Thesis 2019.
Summary: Sharing personal information has become a well-accepted norm for receiving customized and individualized services from the service providers in the cloud. However, sharing of such private and personal information may raise severe privacy violation issues. For example, Autonomous Vehicles (AV) have the potential to fundamentally alter the current transportation systems by making vehicle sharing possible, easy, and affordable. Electronic (eHealth) and Mobile (mHealth) healthcare systems have removed the physical barriers of traditional healthcare systems and made instant and continues patient data collection and sharing possible. These services can only be made possible by sharing of personal information, such as user location data and patient health information, which both are considered highly privacy sensitive. In the first part of this dissertation, we investigate the privacy preservation issues raised by such services, and provide solutions for them. Specifically, we propose a privacy preserving task matching and scheduling framework which makes sharing of the AVs possible without leaking any user location information. For mHealth system, we propose schemes for privacy preserving patient-caregiver communications, and deferentially private patient data release. In the second part, motivated by the dramatic growth in the number of smart mobile devices such as smartphones, and the high amount of sensitive and personal information they contained, we study user-oriented security by protecting smartphones from Lunch-time and Theft attacks. Specifically, we model these attacks using sensing and analysis of wireless signals and propose solutions for detecting and preventing them. Our evaluations on collected and simulated data confirm the effectiveness of our proposed schemes.
- Toward Data Privacy Related To The Internet of Things,
Thamer Altuwaiyan
UMB Thesis 2018.
Summary: In the past years, the number of Internet of Things (IoT) devices has dramatically grown. These IoT devices are equipped with one or more sensors, and connected to the Internet to make them significantly beneficial and attractive to the user. In addition, service providers use these IoT devices to collect users' personal data to provide them with satisfied services and personalized experience. However, using IoT devices to share personal data with the service providers could introduce many privacy risks to users. In this dissertation, we study privacy issues related to the IoT, and we introduce new schemes to enhance the users' privacy when the users use IoT devices. First, we propose a privacy-preserving data query scheme in the home IoT voice system, which enables users to use voice commands for uploading voice data and later retrieving them securely. Second, we propose an efficient privacy-preserving IoT contact tracing scheme for infection detection scheme (EPIC), which enables users to check if they have ever got in contact with an infected user in the past. EPIC employees short-range wireless IoT devices to perform the contact tracing task in a privacy manner. Third, we propose a scheme that supports posting and searching protocols for sharing IoT location-based comments. This scheme allows users to share location-based comments without a need to disclose a user's location to service providers, the user's location represents a physical location for an IoT device. Finally, we evaluate the performances of our proposed schemes by conducting intensive real-world experiments, and we show that our proposed schemes can achieve the privacy, accuracy, and efficiency objectives.
- Efficient Privacy-preserving Ride Sharing Organization for Transferable and Non-transferable Services,
Mahmoud Nabil, Ahmed Sherif, Mohamed Mahmoud, Ahmad Alsharif, and Mohamed Abdallah,
IEEE Transactions on Dependable and Secure Computing (TDSC), Accepted in May 2019.
Summary: Ride-sharing allows multiple persons to share their trips together in one vehicle instead of using multiple vehicles. This can reduce the number of vehicles in the street, which consequently can reduce air pollution, traffic congestion and transportation cost. However, a ride-sharing organization requires passengers to report sensitive location information about their trips to a trip organizing server (TOS) which creates a serious privacy issue. In addition, existing ride-sharing schemes are non-flexible, i.e., they require a driver and a rider to have exactly the same trip to share a ride. Moreover, they are non-scalable, i.e., inefficient if applied to large geographic areas. In this paper, we propose two efficient privacy-preserving ride-sharing organization schemes for Non-transferable Ride-sharing Services (NRS) and Transferable Ride-sharing Services (TRS). In the NRS scheme, a rider can share a ride from its source to destination with only one driver whereas, in TRS scheme, a rider can transfer between multiple drivers while en route until he reaches his destination. In both schemes, the ride-sharing area is divided into a number of small geographic areas, called cells, and each cell has a unique identifier. Each driver/rider should encrypt his trip's data and send an encrypted ride-sharing offer/request to the TOS. In NRS scheme, Bloom filters are used to compactly represent the trip information before encryption. Then, the TOS can measure the similarity between the encrypted trips data to organize shared rides without revealing either the users' identities or the location information. In TRS scheme, drivers report their encrypted routes, an then the TOS builds an encrypted directed graph that is passed to a modified version of Dijkstra's shortest path algorithm to search for an optimal path of rides that can achieve a set of preferences defined by the riders.
- Priority-based and Privacy-preserving Electric Vehicle Dynamic Charging System with Divisible E-Payment,
Mahmoud Nabil, Muhammad Bima, Ahmad Alsharif, Willaim Johnson, Surya Gunukula, Mohamed Mahmoud, and Mohamed Abdalla,
Book chapter in book titled “Smart Cities Cybersecurity and Privacy”, Elsevier, In press, 2018.
Summary: Dynamic charging systems enable moving electric vehicles (EVs) to charge using magnetic induction from charging pads (CPs) installed on roads. For the system to function, the EVs need to communicate with the various entities of the system, which include a bank, a charging service provider (CSP), roadside units (RSUs), and CPs. This communication should not reveal sensitive location information about the EV drivers, and security should also be thoroughly investigated to ensure proper operation of the system. In this chapter, we present a scheme that provides integrated, secure, and privacy-preserving authentication, prioritization, and payment for dynamic charging. In order to make payment, the EV should first purchase divisible e-coins from the bank and use them when it needs to charge. The payment scheme should be efficient and flexible in that the value of the e-coins can be adjusted based on the amount paid for charging. Charge prioritization is needed when the energy supply is less than the charging demand because the CSP cannot serve all incoming charge requests. In our scheme, a priority policy is determined by each charging station, and a multiauthority, attribute-based encryption scheme is used to ensure the security and privacy of the policy. In order to address the scalability of the system due to the large number of EVs and CPs and the limited resources of the CPs, an efficient hierarchical authentication scheme that is based on symmetric-key cryptography is proposed. The idea is that after an EV authenticates successfully to the CSP, it receives secret keys, called tokens, that are shared with the RSUs. After using these tokens to authenticate to the RSUs, the EV receives secret tokens that are shared with a number of CPs under each RSU control. These tokens are used to enable the CPs to identify and charge only authorized EVs. Our security analysis demonstrates that the proposed scheme is secure and can preserve the privacy of the EV drivers by making identifying the drivers and tracing them infeasible. In addition, performance evaluations confirm that the computational and communication overhead of the scheme is acceptable.
- Privacy-preserving Voice-based Search over mHealth Data,
Mohammad Hadian, Thamer Altuwaiyan, Xiaohui Liang, and Wei Li,
Smart Health Journal, Volume 12, April 2019, Pages 24-34.
Summary: Voice-enabled devices have a potential to significantly improve the healthcare systems as smart personal assistants. They usually come with a hands-free feature to add an extra level of usability and convenience to elderly, disabled people and patients. In this paper, we propose a privacy-preserving voice-based search scheme to enhance the privacy of in-home healthcare applications. We consider an application scenario where patients use the devices to communicate with their caregivers by recording and uploading their voices to the servers, where the caregivers can search the interested voices of their patients based on the voice content, mood, tone and background sounds. Our scheme preserves the richness and privacy of voice data and enables accurate and efficient voice-based search, while in current systems that use speech recognition, the richness and privacy of voice data are compromised. Specifically, our scheme achieves the privacy by employing a privacy-preserving voice feature matching technique and a novel category-based encryption; only encrypted voice data is uploaded to the server who is unable to access the original voice data. In addition, our scheme enables the server to selectively and accurately respond to caregivers' queries on the voice data based on voice similarities. We evaluate our scheme through real experiments and show that our scheme even with privacy preservation can successfully match similar voice data at an average accuracy of 80.8%.
- Energy Theft Detection with Energy Privacy Preservation in the Smart Grid,
Donghuan Yao, Mi Wen, Xiaohui Liang, Zipeng Fu, Kai Zhang, and Baojia Yang,
IEEE Internet of Things Journal, 2019.
Summary: As a prominent early instance of the IoT in the smart grid, the advanced metering infrastructure (AMI) provides real-time information from smart meters to both grid operators and customers, exploiting the full potential of demand response. However, the newly-collected information without security protection can be maliciously altered and result in huge loss. In this paper, we propose an energy theft detection scheme with energy privacy preservation in the smart grid. Specially, we use combined convolutional neural networks (CNN) to detect abnormal behavior of the metering data from a long-period pattern observation. In addition, we employ Paillier algorithm to protect the energy privacy. In other words, the users’ energy data are securely protected in the transmission and the data disclosure is minimized. Our security analysis demonstrates that in our scheme data privacy and authentication are both achieved. Experimental results illustrate that our modified CNN model can effectively detect abnormal behaviors at an accuracy up to 92.67%.
- Revealing Your Mobile Password via WiFi Signals: Attacks and Countermeasures,
Yan Meng, Jinlei Li, Haojin Zhu, Xiaohui Liang, Yao Liu, and Na Ruan,
IEEE Transactions on Mobile Computing, 2019.
Summary: In this study, we present WindTalker, a novel and practical keystroke inference framework that can be used to infer the sensitive keystrokes on a mobile device through WiFi-based side-channel information. WindTalker is motivated from an observation that keystrokes on mobile devices will lead to different hand coverage and the finger motions, which will introduce a unique interference to the multi-path signals and can be reflected by the channel state information (CSI). Compared with the previous keystroke inference approaches, WindTalker neither deploys external equipment physically close to the target device nor compromises the target device. In addition, to improve inference accuracy and efficiency, it analyzes the WiFi traffic to selectively collect CSI only for the sensitive period where password entering occurs. We tested Windtalker on several mobile phones and performed a detailed case study to evaluate the practicality of the password inference towards Alipay, the largest mobile payment platform in the world. Furthermore, we proposed a novel CSI obfuscation countermeasure to thwart the inference attack. The evaluation results show that the attacker can recover the key with a high successful rate in the current system, and the successful rate is largely reduced by the proposed countermeasure.
- SmartEye: Mobile Device Proximity Monitoring via Wireless Signal Analysis,
Mohammad Hadian, T. Altuwaiyan, Xiaohui Liang, Bo Sheng, and Kuan Zhang,
ICNC — IEEE International Conference on Computing, Networking and Communications, 2019.
Summary: Mobile devices are pervasively used by everyone in all aspects of their daily lives. Sensing capability of the mobile devices, using their built-in sensors, is usually limited to their immediate proximity. In this paper, we exploit a technique which enables the mobile device to sense its physical proximity by taking advantage of the WiFi Channel State Information. We define a model to detect the movements of human and non-human objects in the proximity of the device. We have exploited the Fresnel zone model to detect the movement towards and outwards the device in the sensing area. The scheme can be used to alarm the user when device is left unattended. We further consider two models for early-detection of a user leaving her mobile device based on the user requirements and environment conditions. We evaluate our scheme using information from simulated theft attack scenarios in real environment and show that our scheme can achieve an average 84.44% and 77.77% accuracy on detecting the theft attacks for outdoor and indoor environments respectively.
- Blockchain-based Privacy-Preserving Charging Coordination Mechanism for Energy Storage Units,
Mohamed Baza, Mahmoud Nabil, Muhammad Ismail, Mohamed Mahmoud, Erchin Serpedin, and Mohammad Rahman,
Recent Advances on Blockchain and Its Applications Symposium of the 2nd IEEE International Conference on Blockchain (Blockchain-2019), Atlanta, USA, July 2019.
Summary: Energy storage units (ESUs) enable several attractive features of modern smart grids such as enhanced grid resilience, effective demand response, and reduced bills. However, uncoordinated charging of ESUs stresses the power system and can lead to a blackout. On the other hand, existing charging coordination mechanisms suffer from several limitations. First, the need for a central charging coordinator (CC) presents a single point of failure that jeopardizes the effectiveness of the charging coordination. Second, a transparent charging coordination mechanism does not exist where users are not aware whether the CC is honest or not in coordination charging requests among them in a fair way. Third, existing mechanisms overlook the privacy concerns of the involved customers. To address these limitations, in this paper, we leverage the blockchain and smart contracts to build a decentralized charging coordination mechanism without the need for a centralized charging coordinator. First ESUs should use tokens for anonymously authenticate themselves to the blockchain. Then each ESU sends a charging request that contains its State-of-Charge (SoC), Time-to-complete-charge (TCC) and amount of required charging to the smart contract address on the blockchain. The smart contract will then run the charging coordination mechanism in a self-executed manner such that ESUs with the highest priorities are charged in the present time slot while charging requests of lower priority ESUs are deferred to future time slots. In this way, each ESU can make sure that charging schedules are computed correctly. Finally, we have implemented the proposed mechanism on the Ethereum test-bed blockchain, and our analysis shows that execution cost can be acceptable in terms of gas consumption while enabling decentralized charging coordination with increased transparency, reliability, and privacy preserving.
- Blockchain-based Firmware Update Scheme Tailored for Autonomous Vehicles,
Mohamed Baza, Mahmoud Nabil, Noureddine Lasla, Kemal Fidan, Mohamed Mahmoud, and Mohamed Abdallah,
IEEE Wireless Communications and Networking Conference (WCNC), Marrakech, Morocco, April 2019.
Summary: Recently, Autonomous Vehicles (AVs) have gained extensive attention from both academia and industry. AVs are a complex system composed of many subsystems, making them a typical target for attackers. Therefore, the firmware of the different subsystems needs to be updated to the latest version by the manufacturer to fix bugs and introduce new features, e.g., using security patches. In this paper, we propose a distributed firmware update scheme for the AVs' subsystems, leveraging blockchain and smart contract technology. A consortium blockchain made of different AVs manufacturers is used to ensure the authenticity and integrity of firmware updates. Instead of depending on centralized third parties to distribute the new updates, we enable AVs, namely distributors, to participate in the distribution process and we take advantage of their mobility to guarantee high availability and fast delivery of the updates. To incentivize AVs to distribute the updates, a reward system is established that maintains a credit reputation for each distributor account in the blockchain. A zero-knowledge proof protocol is used to exchange the update in return for a proof of distribution in a trust-less environment. Moreover, we use attribute-based encryption (ABE) scheme to ensure that only authorized AVs will be able to download and use a new update. Our analysis indicates that the additional cryptography primitives and exchanged transactions do not affect the operation of the AVs network. Also, our security analysis demonstrates that our scheme is efficient and secure against different attacks.
- WiVo: Enhancing the Security of Voice Control System via Wireless Signal in IoT Environment,
Yan Meng, Zichang Wang, Wei Zhang, Peilin Wu, Haojin Zhu, Xiaohui Liang, and Yao Liu,
MobiHoc 2018.
Summary: With the prevalent of smart devices and home automations, voice command has become a popular User Interface (UI) channel in the IoT environment. Although Voice Control System (VCS) has the advantages of great convenience, it is extremely vulnerable to the spoofing attack (e.g., replay attack, hidden/inaudible command attack) due to its broadcast nature. In this study, we present WiVo, a device-free voice liveness detection system based on the prevalent wireless signals generated by IoT devices without any additional devices or sensors carried by the users. The basic motivation of WiVo is to distinguish the authentic voice command from a spoofed one via its corresponding mouth motions, which can be captured and recognized by wireless signals. To achieve this goal, WiVo builds a theoretical model to characterize the correlation between wireless signal dynamics and the user’s voice syllables. WiVo extracts the unique features from both voice and wireless signals, and then calculates the consistency between these different types of signals in order to determine whether the voice command is generated by the authentic user of VCS or an adversary. To evaluate the effectiveness of WiVo, we build a testbed based on Samsung SmartThings framework and include WiVo as a new application, which is expected to significantly enhance the security of the existing VCS. We have evaluated WiVo with 6 participants and different voice commands. Experimental evaluation results demonstrate that WiVo achieves the overall 99% detection rate with 1% false accept rate and has a low latency.
- Efficient and Privacy-preserving Roadmap Data Update for Autonomous Vehicles,
Haoyu Wang, Mohammad Hadian, and Xiaohui Liang,
IEEE GLOBECOM 2018.
Summary: Autonomous vehicles (AV) need an access to a big amount of data from online roadmap servers and local sensors to make real-time control decision for safety. Considering the roadmap data may change in cases of road maintenance, new/broken road signs, accidents, traffic jams, AV should keep its local roadmap data updated with the online roadmap servers. In this paper, we propose an efficient and privacy-preserving roadmap data update scheme for AV, which achieves the privacy preservation of route information while minimizing the update overhead. We define a new type of privacy sensitivity of a road segment based on its three properties, hotspot sensitivity, proximity sensitivity, and route sensitivity. We then define a new type of k-anonymity protection on road segment, i.e., to protect a target segment with sensitivity l, the anonymity segment set must include at least k-1 segments with sensitivity ≥ l. In addition, we consider for a more sensitive segment, k needs to be larger to protect the segment. Finally, this scheme, by considering different privacy features, achieves the required privacy preservation at a lower bandwidth cost compared to the traditional k-anonymity mechanism due to prioritizing the selection of the most sensitive anonymity segments. Based on the roadmap data from Google Map, we evaluated our scheme for roadmap data update and route conditions and showed a trade-off between the route privacy preservation and the communication overheads.
- EPIC: Efficient Privacy-preserving Contact Tracing for Infection Detection,
Thamer Altuwaiyan, Mohammad Hadian, Xiaohui Liang, and Wei Li,
IEEE ICC 2018.
Summary: The world has experienced many epidemic diseases in the past, SARS, H1N1, and Ebola are some examples of these diseases. When those diseases outbreak, they spread very quickly among people and it becomes a challenge to trace the source in order to control the disease. In this paper, we propose an efficient privacy-preserving contact tracing for infection detection (EPIC) which enables users to securely upload their data to the server and later in case of one user got infected other users can check if they have ever got in contact with the infected user in the past. The process is done privately and without disclosing any unnecessary information to the server. Our scheme uses a matching score to represent the result of the contact tracing, and uses a weight-based matching method to increase the accuracy of the score. In addition, we have developed an adaptive scanning method to optimize the power consumption of the wireless scanning process. Further, we evaluate our scheme in real experiment and show that the user's privacy is preserved, and the accuracy achieves 93% in detecting the contact tracing based on the matching score in an energy efficient way.
- Efficient Privacy-Preserving Aggregation Scheme for Data Sets,
Ahmed Sherif, Ahmad Alsharif, Mohamed Mahmoud, Mohamed Abdallah, and Min Song,
IEEE International Conference on Telecommunication (ICT), France, June 2018.
Summary: Many applications depend on privacy-preserving data aggregation schemes to preserve users' privacy. The main idea is that no entity should be able to access users' individual data to preserve privacy, but the aggregated data should be known for the application functionality. In these schemes, each user should encrypt a message and send it to an aggregator to compute and send the ciphertext of the aggregated messages to the decryptor without learning the individual messages. The decryptor should decrypt the ciphertext to obtain the aggregated message. However, the existing schemes are designed to aggregate one type/size of data and it is inefficient to modify them to aggregate messages that have data sets of different data types and sizes. In this paper, we propose an efficient privacy-preserving aggregation scheme for data sets. Unlike the existing schemes that do multibit number addition, the proposed scheme aggregates individual bits. Moreover, comparing to the existing schemes, our scheme has two new features. First, in some applications (such as those that need reporting location information), the aggregator can verify the encrypted messages to detect data pollution attacks without accessing the messages to preserve privacy. Second, our scheme has two types of decryptions; called full and partial. In full decryption, the decryptor can decrypt the whole data set, while in partial decryption, the decryptor can enable some entities to decrypt some data in the set. Our analysis demonstrates that the proposed scheme is secure and can preserve users' privacy. Extensive experimental results demonstrate that our scheme is more efficient than the existing schemes.
- Performance Analysis of Physical-layer-based Authentication for Electric Vehicle Dynamic Charging,
Terry Guo and Mohamed Mahmoud,
IEEE 88th Vehicular Technology Conference (VTC-Fall) 2018.
Summary: Electric Vehicle (EV) dynamic charging is a new charging technology that has received attention recently from both industry and academia. It is much convenient compared to plug-in power charging. However, the EVs need to pay and authenticate to charging pads placed on roads to get charged. because of its wireless and fast moving nature, dynamically offering services (including secure and reliable payment based access, power charging, etc.) to the paid users is challenging. In an efficient physical-layer-based authentication scheme, the EVs should sent digital secret token to the pads that should verify them. To design a scheme that meets both security and reliability requirements in EV dynamic charging scenario, this paper analyzes and evaluates the verification performance. Probabilistic performance metrics are defined and an analytic framework is developed to quantify the performance. The derived estimation formulas are validated by numerical results, and these results reveal the sensitive impacts of token-pool Hamming distance, decision threshold and Signal-to-Noise Ratio (SNR).
- Privacy-preserving Route Reporting Schemes for Traffic Management Systems,
Khaled Rabieh, Mohamed Mahmoud, and Mohamed Younis,
IEEE Transactions on Vehicular Technology (TVT), Vol. 66 , No. 3, 2017.
Summary: In this paper, we propose privacy-preserving route reporting schemes for traffic management for both infrastructure-supported and self-organizing vehicular ad hoc networks (VANETs). Using only pseudonyms and anonymous authentication to conceal the real identity of the drivers cannot fully preserve the drivers' privacy because the reported future positions can be used to link pseudonyms and identify the drivers, e.g., from the locations they visit. Motivated by the fact that traffic management systems do not need to know the vehicles' individual routes and the total number of vehicles in each road segment would suffice, the proposed schemes aggregate the vehicles' routes. Countering the collusion attacks is usually hard, particularly in a self-organizing setting. The concept we use to mitigate the attack is that one vehicle is not trusted to run the scheme because it can be curious to know the drivers' routes, but these schemes are run by multiple vehicles. Our ns-2 simulation results and analysis have demonstrated that our schemes can preserve the drivers' privacy with acceptable overhead.
- Privacy-preserving Ride Sharing Scheme for Autonomous Vehicles in Big Data Era,
Ahmed Sherif, Khaled Rabieh, Mohamed Mahmoud, and Xiaohui Liang,
IEEE Internet of Things Journal, vol. 4, no. 2, pp. 611-618, 2017.
Summary: Ride sharing can reduce the number of vehicles in the streets by increasing the occupancy of vehicles, which can facilitate traffic and reduce crashes and the number of needed parking slots. Autonomous vehicles can make ride sharing convenient, popular, and also necessary because of the elimination of the driver effort and the expected high cost of the vehicles. However, the organization of ride sharing requires the users to disclose sensitive detailed information not only on the pick-up/drop-off locations but also on the trip time and route. In this paper, we propose a scheme to organize ride sharing and address the unique privacy issues. Our scheme uses a similarity measurement technique over encrypted data to preserve the privacy of trip data. The ride sharing region is divided into cells and each cell is represented by one bit in a binary vector. Each user should represent trip data as binary vectors and submit the encryptions of the vectors to a server. The server can measure the similarity of the users' trip data and find users who can share rides without knowing the data. Our analysis has demonstrated that the proposed scheme can organize ride sharing without disclosing private information. We have implemented our scheme using Visual C on a real map and the measurements have confirmed that our scheme is effective when ride sharing becomes popular and the server needs to organize a large number of rides in short time.
- Privacy-preserving Fine-grained Data Retrieval Scheme for Mobile Social Networks (MSNs),
Mohamed Mahmoud, Khaled Rabieh, Ahmed Sherif, Enahoro Oriero, Muhammad Ismail, Khalid Qaraqe, and Erchin Serpedin,
IEEE Transactions on Dependable and Secure Computing (TDSC), 2017.
Summary: In this paper, we propose privacy-preserving fine-grained data retrieval schemes for mobile social networks (MSNs). The schemes enable users to retrieve data from other users who are interested in some topics related to a subject of interest. We define a subject to be a broad term that can cover many fine-grained topics, e.g., History can be a subject and World War I can be a topic. We consider centralized and decentralized network models. Our centralized scheme allows users to securely outsource data to a server such that the server matches the users who are interested in same topic(s) and have defined social attributes with privacy preservation. Searchable encryption scheme and a proposed cryptography construct are used to enable the server to match the topics and attributes without knowing any private information. By using the social attributes, users can prescribe the other users who can be connected to. We also propose a decentralized scheme that can be used when there is no connection to the server, i.e, shortage of Internet connectivity. The scheme leverages friends-of-friends relationship and transferable trust concept, where each user trusts his friends and the friends of friends. If a friend is not interested in the requested subject, he/she can link him/her to his/her friends without knowing the requested subject to preserve privacy. Our schemes use Bloom filters to store the topics of interest to reduce the storage and communication overhead. This is important because the number of fine-grained topics can be large. Different techniques to store the topics in the filter are proposed and investigated. Performance metrics are proposed and evaluated using real implementations. Our analysis and implementation results demonstrate that our schemes can preserve the privacy of the MSN users with high performance.
- Re-DPoctor: Real-time Health Data Releasing with w-day Differential Privacy,
Jiajun Zhang, Xiaohui Liang, Zhikun Zhang, Shibo He, and Zhiguo Shi,
IEEE GLOBECOM 2017.
Summary: Wearable devices enable users to collect health data and share them with healthcare providers for improved health service. Since health data contain privacy-sensitive information, unprotected data release system may result in privacy leakage problem. Most of the existing work use differential privacy for private data release. However, they have limitations in healthcare scenarios because they do not consider the unique features of health data being collected from wearables, such as continuous real-time collection and pattern preservation. In this paper, we propose Re-DPoctor, a real-time health data releasing scheme with w-day differential privacy where the privacy of health data collected from any consecutive w days is preserved. We improve utility by using a specially-designed partition algorithm to protect the health data patterns. Meanwhile, we improve privacy preservation by applying newly proposed adaptive sampling tech- nique and budget allocation method. We prove that Re-DPoctor satisfies w-day differential privacy. Experiments on real health data demonstrates that our method achieves better utility with strong privacy guarantee than existing state-of-the-art methods.
- Efficient and Privacy-preserving Voice-based Search over mHealth Data,
Mohammad Hadian, Thamer Altuwaiyan, Xiaohui Liang, and Wei Li,
The International Workshop on Security, Privacy, and Trustworthiness in Medical Cyber Physical Systems 2017.
Summary: In-home IoT devices play a major role in healthcare systems as smart personal assistants. They usually come with a voice-enabled feature to add an extra level of usability and convenience to elderly, disabled people, and patients. In this paper, we propose an efficient and privacy-preserving voice-based search scheme to enhance the efficiency and the privacy of in-home healthcare applications. We consider an application scenario where patients use the devices to record and upload their voice to servers and the caregivers search the interested voices of their patient's based on the voice content, mood, tone and background sound. Our scheme preserves the richness and privacy of voice data and enables accurate and efficient voice-based search, while in current systems that use speech recognition the richness and privacy of voice data are compromised. Specifically, our scheme achieves the privacy by employing a homomorphic encryption; only encrypted voice data is uploaded to the server who is unable to access the original voice data. In addition, our scheme enables the server to selectively and accurately respond to caregiver's queries on the voice data based on voice's feature similarity. We evaluate our scheme through real experiments and show that our scheme even with privacy preservation can successfully match similar voice data at an average accuracy of 80.8%.
- Efficient Certificate Verification for VehicletoGrid Communications,
Nico Saputro, Samet Tonyali, Kemal Akkaya, Mumin Cebe, and Mohamed Mahmoud,
The 3rd International Conference on Future Network Systems and Security (FNSS), 31 August 2 September 2017, Gainesville, Florida, USA.
Summary: While public charging stations are typically used for Electric Vehicle (EV) such as charging, home microgrids that may act as private charging stations are also expected to be used for meeting the increased EV charging demands in the future. Such home microgrids can be accessible through their smart meters, which makes advanced metering infrastructure (AMI) a viable alternative for vehicle-to-grid (V2G) communications. However, to ensure secure V2G communications using public-keys, smart meters will need to maintain certificate revocation lists (CRLs) not just for the AMI network but also for large number of EVs that may interact with them. For resource-constrained smart meters, this will increase the storage requirements and introduce additional overhead in terms of delay and CRL maintenance. To eliminate this burden, we propose keeping merely non-revoked certificates that belong to EVs, which are usually driven within the vicinity of that particular microgrid. The motivation comes from the fact that it is inefficient to distribute and store a large CRL that has revocation information about all EVs in the whole system as most of these EVs will never come to the geographic vicinity of that home microgrid. The approach ensures that any status changes of these certificates are communicated to the smart meters. We implemented the proposed approach in a realistic V2G communication scenario by using IEEE 802.11s mesh as the underlying AMI infrastructure using ns-3 simulator. The results confirmed that the proposed approach significantly reduces the certificate verification time and the storage requirements on smart meters.
- Privacy-preserving Time-sharing Services for Autonomous Vehicles,
Mohammad Hadian, Thamer Altuwaiyan, and Xiaohui Liang,
IEEE Vehicular Technology Conference (VTC), 2017.
Summary: Sharing the Autonomous Vehicles (AV) has the potential to be the ultimate solution for overcoming the cost problem of these type of vehicles to fundamentally change the transportation systems. AVs enable the time sharing services where AV owners share their AVs at the times they don't need them. Such sharing could reduce the cost by enabling the owner to share the cost of the vehicle with other users. However, these services raise a severe privacy concern as the shared location and route data of the users are considered highly private and sensitive. In this paper we propose a privacy- preserving time-sharing scheme for AVs. Our approach enables the owner and the requester to perform a privacy-preserving matching on their transportation needs over the server without disclosing their routes to the server. To do so we use a set of Points of Interest (POI) locations as intermediate destinations in travel paths. Only if the matching is conflict-free and efficient, the owner and the requester share the details of the routes. We also show the accuracy of the proposed approach through extensive simulations on real data. It is shown that our enhanced POI selection scheme, with consideration of the traffic information and patterns in the area, outperforms the baseline scheme where the POIs are chosen randomly. Furthermore, it shows that our scheme achieves high accuracy in terms of resulting in false negatives compared to the ground truth.
- Privacy-preserving Ride Sharing Organization Scheme for Autonomous Vehicles in Large Cities,
Ahmed Sherif, Ahmad Alsharif, Jacob Moran, and Mohamed Mahmoud,
IEEE Vehicular Technology Conference (VTC), 2017.
Summary: The autonomous vehicles will make ride sharing popular, and necessary. However, ride sharing organization requires the passengers to reveal sensitive information about their trips, which causes a serious privacy issue. In this paper, we propose a privacy-preserving ride sharing organization scheme using the kNN encryption scheme, Bloom filter, and group signature. Each user encrypts his trip's data and sends an encrypted ride-sharing request to a server that measures the similarity between users trips' to organize shared rides without revealing sensitive information. Comparing to our proposal in [1], this paper has three improvements. The proposed scheme is much more efficient because the trip data is much shorter. It is also more secure because each user has his own encryption key instead of using one shared key for all users. It can prevent linking the encryptions of the trip's data sent at different times because users frequently update their keys efficiently. Our privacy analysis demonstrates that the proposed scheme can preserve users' location privacy and trips' data privacy. Our experimental results on a real map demonstrate that the proposed scheme is much more efficient than the existing schemes, especially for large cities.
- Privacy-preserving Intra-MME Group Handover Via MRN in LTEA Networks for Repeated Trips,
Zaher Haddad, Ahmad Alsharif, Ahmed Sherif, and Mohamed Mahmoud,
IEEE Vehicular Technology Conference (VTC), 2017.
Summary: In Long Term Evolution-Advanced (LTE-A) networks, Mobile Relay Nodes (MRNs) are installed in fast moving buses and trains to connect the passengers' devices to evolved Node B (eNB). However, since the MRNs and eNBs are installed in open environment, they can be compromised to launch security and privacy attacks. In this paper, we propose a privacy preserving intra Mobility Management Entity (MME) group handover scheme in LTE-A networks for repeated trips. Comparing to the existing schemes, the proposed scheme is devised to achieve the following requirements. First, the MRNs should be able to authenticate the received messages so that the messages sent from external attackers can be dropped by the MRNs rather than forwarding them to the core network. Second, the proposed scheme also aims to reduce the computational and signaling overhead and establish secure session keys. Third, the scheme aims to prevent MRNs and eNBs from tracking passengers' locations especially if they take same trip regularly. Our analysis demonstrates that the proposed scheme can achieve our security and privacy objectives. Our performance evaluations demonstrate that the proposed scheme requires a few number of messages and low computation overhead.
- Privacy-preserving mHealth Data Release with Pattern Consistency,
Mohammad Hadian, Xiaohui Liang, Thamer Altuwaiyan, and Mohamed Mahmoud,
IEEE Global Communications Conference (GLOBECOM) 2016.
Summary: Mobile healthcare system integrating wearable sensing and wireless communication technologies continuously monitors the users' health status. However, the mHealth system raises a severe privacy concern as the data it collects are private information, such as heart rate and blood pressure. In this paper, we propose an efficient and privacy-preserving mHealth data release approach for the statistic data with the objectives to preserve the unique patterns in the original data bins. The proposed approach adopts the bucket partition algorithm and the differential privacy algorithm for privacy preservation. A customized bucket partition algorithm is proposed to combine the database value bins into buckets according to certain conditions and parameters such that the patterns are preserved. The differential privacy algorithm is then applied to the buckets to prevent an attacker from being able to identify the small changes at the original data. We prove that the proposed approach achieves differential privacy. We also show the accuracy of the proposed approach through extensive simulations on real data. Real experiments show that our partitioning algorithm outperforms the state-of-the-art in preserving the patterns of the original data by a factor of 1.75.
Disclaimer: The papers here are made available for timely dissemination of scholarly and technical work. Copyright and all rights therein are retained by authors or by other copyright holders.
Links to Code Repositories
At University of Massachusetts Boston:
- [Link] We studied an existing IoT Simulator which allows user simulating the activities of sharing data in multiple scenarios. Particularly, we customized the simulator for simulating the autonomous vehicle (AV) time-sharing services. The simulator was built with the geographic map database of Google and enables us to evaluate the proposed technique with or without privacy-preserving techniques using real-time traffic. In other IoT scenarios, we evaluated the data communication of simulated IoT devices based on different metrics such as delay, packet loss, and useful payload in scenarios of encrypted or unencrypted communication.
Curriculum Development
At University of Massachusetts Boston:
- CS 413/613 in Spring 2019, Spring 2020, Spring 2021 (Syllabus, Schedule): Applied Cryptography (covers the fundamental cryptographical techniques used for privacy preservation)
- CS 442/642 in Spring 2018, Spring 2019, Spring 2020, Fall 2020 (Syllabus, Schedule): Cybersecurity in the Internet of Things (covers the privacy analysis of the autonomous vehicular systems and applications)
At Tennessee Technological University:
- ECE 7970: Advanced Cryptography Applications In Emerging Wireless Networks
- The project also has been integrated with an active REU
Outreach
At University of Massachusetts Boston:
- April 14, 2020 - Xiaohui introduced his project on UMass Boston CSM Virtual Welcome Day
- January 6-7, 2020 - Xiaohui attended 2020 NSF Smart Connected Health (SCH) Annual PI meeting in Alexandria, VA.
- November 4-5, 2019 - Xiaohui attended NSF CSR/NeTS 2019 Joint PI Meeting in Arlington, VA.
- October 25, 2019 - Xiaohui gave a talk "VoiceForHealth: Exploring Voice Assistant Systems for Mobile Healthcare" at UMass Dartmouth, MA.
Note: Any opinions, findings and conclusions or recommendations expressed on this website are those of the author(s) and do not necessarily reflect the views of the National Science Foundation (NSF).
|
| |
|
|












